Nikto Cheat Sheet
Running a Nikto web server scan is a straight forward process. Follow through this Nikto Tutorial to get an overview of what is involved. Start your web server testing with one of the most well known website / server testing tools. This is the same tool we use in our hosted Nikto scanner service.
Nikto is a perl based security testing tool and this means it will run on most operating systems with the necessary Perl interpreter installed. We will guide you through using it on Ubuntu Linux, basically because it is our operating system of choice and it just works. Perl comes already installed in Ubuntu. So it is a matter of downloading the tool, unpacking it and running the command with the necessary options. For Windows users running Nikto will involve installing a perl environment (activestate perl) or loading up a Linux virtual machine using Virtualbox or VMware.
- Online Vulnerability Scanners to map the attack surface and identify vulnerabilities. 28 trusted open source security scanners and network tools.
- Use Wappalyzer to identify technologies, web server, OS, database server deployed. View-Source of pages to find interesting comments, directories, technologies, web application being used, etc.
- To supplement the hacking courses on our Cyber Security Career Development Platform, here is our Hacking Tools Cheat Sheet. PDF download also available. Basic Linux Networking ToolsShow IP configuration:# ip a lwChange IP/MAC address:# ip link set dev eth0 down# macchanger -m 23:05:13:37:42:21 eth0# ip link set dev eth0 upStatic IP address configuration:# ip addr add.
- Cheat Sheets 1 Comment DO NOT USE NIKTO OR ANY OTHER TOOL TO SCAN HOST (S) WITHOUT WRITTEN PERMISSION OF THE HOST's OWNER NIKTO SCANNING Scanning a hostNikto -h Scanning specific portsNikto -h -port.
If you are running Microsoft Windows as your main operating system you may find having a virtual machine with Kali Linux or Ubuntu will bring a number of benefits. For a starters it makes getting tools such as Nikto a very simple process, as well as develop some skills using Linux based operating system that will benefit all aspects of your security testing. The majority of free security testing tools are developed on and for Linux based systems. By using a virtual machine you can test Nikto and many other open source security tools without affecting your production workstation.
Nikto Installation on Ubuntu
Nikto Cheat Sheet Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers.
On a default installation of Ubuntu, launch a terminal and using a standard user account download the latest version of Nikto.
You can unpack it with an archive manager tool or use tar and gzip together with this command.
You should see the following output after running nikto.plThis should be your results from a working installation:
If there are any errors regarding SSL support it may be necessary to apt install libnet-ssleay-perl. Without SSL/TLS support you will not be able to test sites over HTTPS.
Starting a Nikto Web Scan
For a simple test we will use test a single host name. In the example below we are testing the virtual host (nikto-test.com) on 16x.2xx.2xx.1xx over HTTPS. The web server on the target responds to the Nikto tests as it would any request to the web server, we can see from the results that the target is a WordPress based site.
In the output we can see the items that were detected as interesting by Nikto. As well as the time taken for the scan and total number of items tested. If we review the web server logs we will be able to see the different items that were tested by the scanner.
Nikto and the Web Server
Lets review the web server logs. An important thing to understand when testing a site with Nikto is the amount of noise that this creates in the web server log files. Essentially Nikto is testing for the presence of thousands of possible web paths, and checking the response from the web server - which for most items will be a 404 not found.
Here is a sample from an Nginx web server being tested by Nikto.
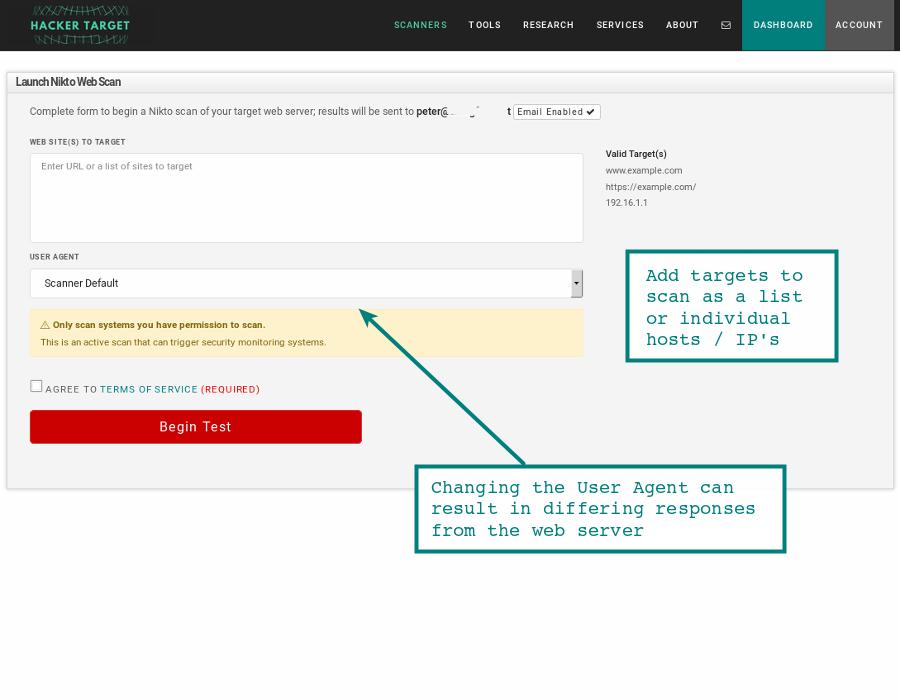
Now unless your intrusion detection or server monitoring is broken, over 5000 of these sorts of hits in the web log will probably trigger a few alarms. Now it is very unlikely that these will cause an impact on the server, but it is certainly easy to spot. We can see the Nikto User Agent is in the log entry. Check the documentation to change the user agent.
Selecting the Target
Since the tool is checking for valid paths, it is important to remember that hitting a web server on different virtual host names, directly on the IP address and even on sub paths off the root of the site will give different results.
Lets take an example of PHPMyAdmin, this is a common tool for managing MySQL databases and can also be a good target for an attacker if it has not been patched or poorly managed. This application could be installed and available at https://2xx.xxx.xxx.xxx/phpmyadmin/ or https://mywebsite.com/phpmyadmin/ or http://mywebsite.com/admin/phpmyadmin/. So to find this application using Nikto we would have to target all three locations, and some servers might have hundreds of virtual hosts.
I am not suggesting running Nikto hundreds of times against every server, but consideration should be taken as to where to target the scan most effectively. Similar considerations come into play when performing simple file / directory brute forcing using Burp Suite or other web application testing tools.

Further information can be found in the documentation on the project page https://cirt.net/nikto2-docs/installation.html
Conclusion
Nikto continues to be an excellent web server testing tool, finding all sorts of obscure issues whether its directory indexing, admin panels or remote code execution in a rare web application. Take the time to run it and be surprised.
- Hacking/OSCP Cheatsheet
- Enumeration
- Network discoverie
- Ports discovery (without nmap)
- Banner grabbing (without nmap)
- Web directorie/file scanner
- Samba
- Exfiltration
- Samba
- HTTP
- Pivoting
- sshuttle
- Reverse shells
- Privilege escalation
- Windows
- Linux
- Good to know (either Windows and/or Linux)
- Simple Buffer Overflow (32 bits, NO ASLR and NO DEP)
- Usefull tools (on Kali Linux)
- Enumeration
Well, just finished my 90 days journey of OSCP labs, so now here is my cheatsheet of it (and of hacking itself), I will be adding stuff in an incremental way as I go having time and/or learning new stuff.But this is basically the tools I tend to relie and use in this way the most.Hope is helpfull for you!
Enumeration
Network discoverie
Nmap
I tend to run 3 nmaps, an initial one, a full one and an UDP one, all of them in parallel:
Is also possible to specify scripts or ports:
If there are servers that could be not answering (ping), then add the flag -Pn (example of initial one):
Ports discovery (without nmap)
nc + bash
If you get in a machine that doesn’t have nmap installed, you can do a basic discovery of (for example), top 10 ports open in 192.168.30 by doing:
/dev/tcp/ip/port or /dev/udp/ip/port
Alternatively, is possible to do the same than above but by using the special dev files /dev/tcp/ip/port or /dev/udp/ip/port (for example nc is not found):
Taking these last examples, is straightforward to create a dummy script for scan a hole /24 net (for example):
Banner grabbing (without nmap)
If nmap didn’t grab banners (or is not installed), you can do it with /dev/tcp/ip/port/dev/udp/ip/port or by using telnet.
/dev/tcp/ip/port or /dev/udp/ip/port
For doing it with udp ports is the same, but changing tcp for udp
telnet
Web directorie/file scanner
Gobuster
Scan all the directories/files by extension:
For scanning without extensions, just take out the -x
Nikto
Sometimes Nikto shows juicy information, I tend to run it like:
fuff
Web fuzzer, you can get fuff here, it basically bruteforces the dirs.
Most usefull dictionaries (OSCP/HTB)
Samba
smbclient
Check if there is anonymous login enabled:
impacket
Is also possible to use impacket in the same way than smbclient to check for anonymous login (and a lot more as browse the shares) in case of incompatible versions.
smbmap
Check which permissions we have in those shares (if there are):
Version (nmap didn’t detect it)
Sometimes nmap doesn’t show the version of Samba in the remote host, if this happens, a good way to know which version the remote host is running, is to capture traffic with wireshark against the remote host on 445/139 and in parallel run an smbclient -L, do a follow tcp stream and with this we might see which version the server is running.
Exfiltration
Samba
Generate a samba server with Impacket:
Mount in Windows
Mounting it in Windows with Powershell:

Mounting it without Powershell:
On windows, to list mounted shares, either Powershell or without it:
Mount in Linux
Is needed to have installed cifs-utils, to install it (in debian based):
To mount it:
To list mounted shares:
HTTP
From your local attacker machine, create a http server with:
It’s also possible to specify which path to share, for example:
Windows
Linux
FTP
If there is an ftp server which we have access, we can upload files there through it, the ' is the same for both, windows or linux:
Sockets
Using nc/ncat is possible to create as a listener to upload/download stuff through them, the syntax for nc and ncat is basically the same.Create the socket with:
RDP
If we have access to a windows machine with a valid user/credentials and this user is in the “Remote Desktop Users”, we can share a local directorie as a mount volume through rdp itself once we connect to the machine:
Pivoting
It’s possible to do pivoting by using proxychains, pure nc’s or in case of linux just some fifo files (I will write them down this another methods down maybe in a future), I have used during all the OSCP an awesome tool called (sshuttle)[https://github.com/sshuttle/sshuttle] (it’s a transparent proxy server that works like “a vpn”, and doesn’t require with super rights, only thing needed is that the bastion server you will use, needs to have installed python) and sometimes some SSH Forwarding. Something worth to mention nmap doesn’t work through sshuttle.
sshuttle
One hop
Let’s say we are in an intranet and we have compromised a firewall that gives us access to the management net (fw.example.mgmt - ips 192.168.20.35 and 192.168.30.253 as the management ip), by using sshuttle we can create a “vpn” to talk directly to those servers, for that, we use:
Multi-hops
Now imagine that after we broke up into the management net after some some enumeration, we ended to compromise a machine that has also access to a production environment (foreman.example.mgmt - ips 192.168.30.40 and 192.168.25.87), we can take advantage of sshuttle + ProxyCommand of ssh to create a “vpn” through this multiple hops, so…putting it down, this will be kind of as follow (the diagram is extremly simplified and just for the sake of illustrate this visually, so it doesn’t intend to provide a 100% precise network diagram):
To have that working, is needed to put the next conf in your ssh conf file (normally ~/.ssh/config. It’s based on the example above, but is easy to extrapolate to different scenarios):
And now to setup the “multiple hop vpn”, run:
Reverse shells
php
bash
sh + nc
Perl (example deploy as cgi-bin)
Java (example to deploy on tomcat)
Windows HTPP download reverse shell
Windows staged reverse TCP
Windows stageless reverse TCP
Linux staged reverse TCP
Linux staged reverse TCP
Privilege escalation
Windows
Run-As
Incorrect permisions in services (sc config binpath)
Binpath is set as running cmd.exe passing a commad to execute to it (so once the process dies, the one executed by it so the command to cmd.exe remains):
SAM + SYSTEM + Security
If those 3 files are in your hands (you could download to your attacker machine), you can dump hashes and crack them:
Linux
/home/user/openssl =ep (empty capabilities)
Make 2 copies of passwd, one as backup of the original, and one that will be used as custom:
Now, a custom user will be created and added to /tmp/passwd.custom with customPassword and as root user (UID = GID = 0):
Now, create a custom key.pem and cert.pem with openssl:
Encrypt the new custom passwd:
Nikto Cheat Sheet 2019
Now, decrypt the custom passwd overwritting in the process the real one (/etc/passwd):
And finally, just login with the user created with root privileges by using customPassword:
Command web injection: add user
NFS; no_root_squash,insecure,rw
If /etc/exports has a line like:
NFS is being exported and you and you have ssh access to the machine.From your attacker machine while logged as root user run:
Now from inside a SSH session on the victim machine (in this example 192.168.42.32):
Good to know (either Windows and/or Linux)
Arch cross compile exploit (and diff glibc version)
IP restriction at application level, bypass
Try to send a request modifying the HTTP header by adding:
Windows - check OS information
Windows - check architecture
Powershell running as 32 or 64 bits
Linux LFI - intesresting files to look after
Simple Buffer Overflow (32 bits, NO ASLR and NO DEP)
Summarized steps
- 0 - Crash the application
- 1 - Fuzzing (find aprox number of bytes where the crash took place)
- 2 - Find offset
- 3 - EIP control
- 4 - Check for enough space on buffer
- 5 - Badchars counting
- 6 - Find return address (JMP ESP)
- 7 - Create payload
Nikto Scan Cheat Sheet
Fuzzing: example with vulnserver + spike on TRUN command
Now, start wireshark filtering on the target IP/PORT below and run the trun.spk:
Once a crash takes place, go to wireshark to locate the crash.
Badchars
Nikto Cheat Sheet Pdf
From the block below, the next ones were not included (most common badchars):
So…actual list of badchars:
Nikto Cheat Sheet Template
Usefull tools (on Kali Linux)
create_pattern
